Cyberwarfare: An Introduction to Information-Age Conflict by Isaac Porche is published by Artech House 2020
Introduction
The book consisting of 13 chapters provides an introductory overview of cyberwarfare as an existing (and new) discipline. Chapter 1 introduces ‘Information and Conflict’ providing key definitions and concepts around:
- Information
- Networks and Technology
- Internet/Web and the information age
- Characteristics of Cyberspace
- Security Terminolgy
- Definitions and descriptions of Cyberspace Operations
- Electronic Warfare and Spectrum operations
- Information Warfare
- Weapons and missions of cyberwar.
DIKW Framework
The DIKW framework is presented which consists of:
- Data: facts, ideas, metrics, signals that individually exist without explict relationships.
- Information: Data that has attributes and relationships associated with it — ‘knowing what’
- Knowledge: Derived inferences from the relationships contained with the Information — ‘knowing how’
- Wisdom: Advanced knowledge and understanding computed or evaluated from the body of knowledge — ‘knowing why’
This DIKW understanding is interesting both in the context of Information Warfare but I also find it a good framework to apply to personal viewpoints and analysis of Information and Operational Technology (IT and OT).
Lifecycle of cyberattack
In Chapter 2, the author introduces the lifecycle of a cyberattack, speaking of offensive cyber operations and the phases of identification of vulnerability access, gaining and maintaining access through a vulnerability and thirdly using access to deliver and execute a payload.
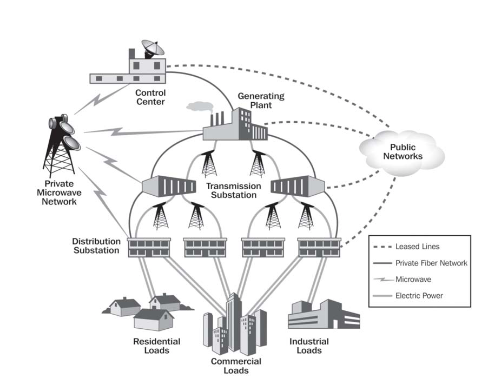
U.S. Department of Homeland Security and U.S. Department of Energy, Energy Sector- Specific Plan: An Annex to the National Infrastructure Protection Plan, 2010, p. 124
Within these attack phases, it should be noted that there is significant planning and preparation effort that is expended prior to the actual intrusion activity.
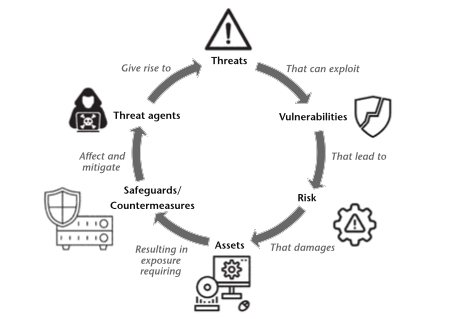
Cyber Risk
In Chapter 3, the author introduces Cyber Risk and it components (loss probability and the loss consequence)
Risk Assessement, Management, Mitigation and Quantative Analysis of risk are discussed with a final discussion of why risk analysis matters and how one should proceed with dealing with cyber risk.
Legal Aspects of Cyber Warefare
In the next chapter the legal aspects of Cyber Warfare and Information Warfare and introduced with areas including:
- Overview of the law of armed conflict
- UN charter
- Violent act of ware within the context of cyber warfare.
- Grayzone and Hybrid Warfare.
- Political norms and Attack attribution.
Chapters 5-9 provides an overview/introduction to:
- Digital and Wireless Communications
- Networking
- Networking Technology including Ethernet, Wifi and bluetooth.
- The Internet Protocol (IP), Transport Layer protocols and Internet Infrastructure.
These introductions are detailed and should be consumable by a general reader and will be common knowledge to most IT professionals.
Offensive Cyber Operations
Chapter 10 introduces Offensive Cyber operations by state actors providing definitions for strategy, tactics, techniques and procedures used in these operations. Background information is provided on the components that may up critical infrastructure within industry (Oil, Gas, Electrcity, Transport, Health, Water, Manufacturing and Pharmacuuticals) which typical have industrial processes that are driven using Industrial Control Systems (ICS).
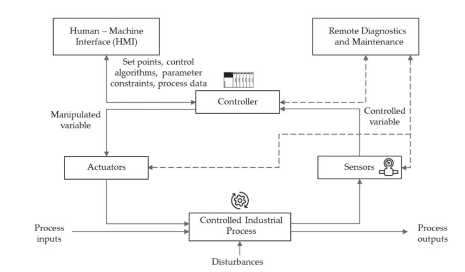
Vulnerabilities, Attacks and Exploits of ICS are explored and the chapter provides a set of case studies that enumerates a number of attacks on ICS systems that are documented and reported in Open Source Intelligence and News sources. The attacked detailed include:
- The Farewell Dossier.
- The Maroochy Shire Sewage Attack.
- Stuxnet.
- Havex.
- Shamoon.
- First Ukraine power outage.
- Second Ukraine power outage.
- Triton.
A brief treatment is also provided of some ransomware attacks including:
- Wannacry.
- NotPetya.
- BadRabbit.
In Chapter 11, the author provides a detailed discussion of Tactics, Techniques and Procedures (TTP) for Offensive cyber operations including discussing the process of an expliotation of web applications.
Chapter 12 provides a discussion of cybersecurity in the maratine domain with Chaper 13 discussing cybersecurity in the US elections (2016)
Final Thoughs
Overall, this is a good introductory text on cyberwarfare which although published in 2020 will be in need of an update based on rapid evolution of events that have ocurred in 2020 and 2021, some areas that I believe that may be future subjects for Mr. Porsche to consider are:
- The Solarwinds compromise, providing a mechanism for exploitation using the tools that IT departments use to operate networks.
- The Colonial pipeline attack, a ransomware attach that crippled a critical component of the supply chain that affected the East Coast of the US.
- Other ransomware attacks that have crippled health care operations such as the attack on the HSE in Ireland.
- Although not a cyberattack, the Even Given/Suez incident and how the worlds supply chain can be disrupted by a single vessel blocking a chokepoint in a global transport network.